Security can’t sit at the end of your pipeline anymore. You already know that. Every delay, missed alert, or manual review increases risk and slows your delivery pipeline.
DevSecOps addresses this by embedding security into every stage of the software development lifecycle. This makes protection an important part of how you build rather than something you bolt on later.
In this article, you’ll see how this approach works in practice and why it matters. So, let’s start by defining it clearly.
What Is DevSecOps?
DevSecOps is a collaborative approach that treats security as code. It embeds security directly into development and operations so you can maintain delivery speed while reducing risk.
Basically, you will integrate automated checks, shared accountability, and continuous verification across the software development process.
And your competitors are likely already taking this approach.
According to Grand View Research, the DevSecOps market will grow from $8.84 billion in 2024 to $20.24 billion by 2030. This growth shows how important integrated security has become for maintaining delivery speed and resilience across modern engineering teams.
What Does DevSecOps Stand For?
DevSecOps stands for development, security, and operations. It connects your development and operations workflows with built-in security from code commit to production.
The main benefit is that you can automate security measures and reduce manual effort while keeping speed and consistency across teams.
What Is the DevSecOps Culture?
The DevSecOps culture means creating shared ownership of security across development, operations, and security functions. It relies on:
- Clear communication
- Well-defined process workflows
- Tools that support CI/CD
Basically, people work as one unit, guided by metrics and automation instead of manual gatekeeping.
Technology supports this mindset by embedding checks for security vulnerabilities into the same pipelines that deliver software.
Your long-term goal should be for this collaboration to replace reactive fixes with proactive prevention. That’s how you maintain delivery speed while strengthening reliability and compliance.
DevSecOps vs. DevOps
DevOps focuses on collaboration between development and operations to accelerate delivery through continuous integration and continuous delivery. DevSecOps, on the other hand, extends that model by embedding security practices directly into each stage of the pipeline.
DevOps’s main goal is delivery performance and reliability. Meanwhile, DevSecOps adds shared responsibility for security to align protection with velocity and trust.
Also, automated checks, policy-as-code, and threat detection tools are added along with manual reviews. This allows you to deploy faster without compromising security and compliance.
What Does DevOps Security Look Like?
DevOps security is built-in, automated, and designed for modern architectures like containers and microservices. It shifts protection left by embedding controls into pipelines, which reduces the need for late-stage reviews.
Automated scans, image validation, and runtime security checks verify each commit and container before deployment. This limits exposure across environments and supports rapid feedback loops.
Instead of manual approvals, you rely on policies and automated tests that run continuously.
That way, you get faster, safer releases with minimal disruption to your workflow.
DevSecOps Benefits
According to DevSecOps.org, the most mature teams integrate security directly into delivery workflows and use automation to maintain consistency.
The main benefits are:
- Finding and fixing issues faster: Automated scans and remediation actions shorten detection and response cycles. A recent survey showed that.
- Reducing risks of attacks: Integrated security gates and testing across pipelines reduce exposure points and lower breach probability. With the average cost of a data breach at $4.45 million, prevention directly impacts ROI.
- Scaling faster: Automated checks and clear ownership across teams reduce pipeline bottlenecks and coordination delays. This can help you maintain speed and consistency even in regulated environments.
Pro tip: If you’re aiming for faster time to market, Axify can help you by connecting engineering performance metrics with delivery outcomes. You can visualize DORA metrics to identify speed and quality issues, and take action before they impact releases.
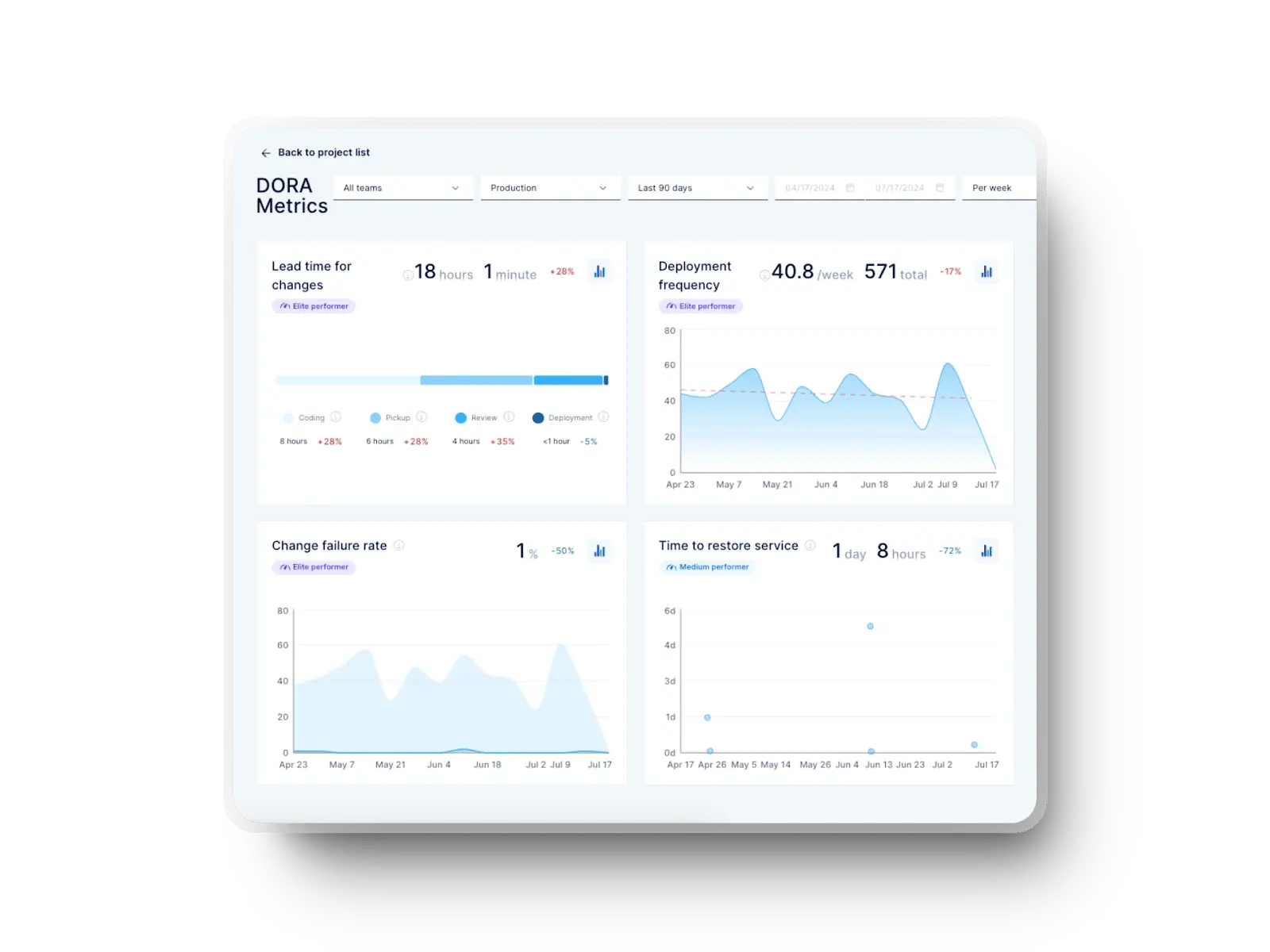
DevSecOps Metrics
Metrics give you visibility into how secure and efficient your delivery process truly is. They help you understand where risks appear, how fast they’re resolved, and whether automation actually improves outcomes.
Here are the key DevSecOps metrics that you should track:
- Mean time to detect (MTTD): Measures how long it takes to identify a security incident after it occurs in production or testing. Lower MTTD means faster awareness and fewer blind spots.
- Mean time to remediate (MTTR), also known as failed deployment recovery time: This shows how long it takes to fix and redeploy after a failed change. In Axify, you can monitor failed deployment recovery time directly through delivery performance dashboards for real-time context.
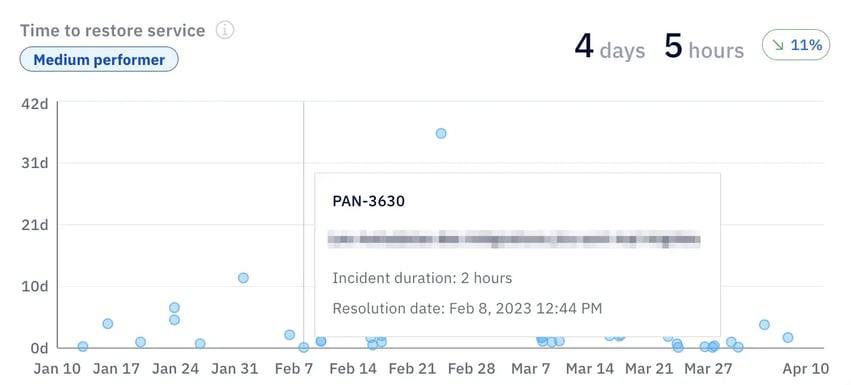
- Security debt: Represents the backlog of unresolved vulnerabilities or unpatched systems. It helps you measure how risk accumulates over time.
- Code coverage: Indicates how much of your application code is tested by automated pipelines and automated test suites. High coverage gives your team confidence that key paths are validated before deployment.
Tracking these metrics together links performance measurement to real improvements in speed, safety, and delivery quality.
Do You Need DevSecOps?
You need DevSecOps if your current development process lacks speed, visibility, or shared accountability across teams. It becomes important when:
- Teams are siloed, and communication breaks down between development, operations, and security.
- Long development cycles delay remediation of risks.
- You’re migrating to the cloud and face greater exposure from distributed systems.
Cloud migrations expose these visibility, coordination, and security challenges.
In fact, 81% of organizations cite security as a major concern during the process. And they’re right to do so, seeing as 80% of companies faced a cloud security incident in 2024.
This proves that reactive protection alone isn’t enough. DevSecOps gives you structured control and automation to prevent these risks before they escalate.
DevSecOps Principles
Strong DevSecOps practices rest on a few core principles that guide how you integrate protection into delivery. These principles, as outlined by Microsoft, focus on keeping security continuous and collaborative rather than reactive. Here are the key ones:
- Continuous integration: Every commit should trigger automated builds and tests. The point is to detect code issues or configuration drift early and avoid costly rework later in the pipeline. It also creates consistent visibility across teams so everyone can track quality in real time.
- Continuous delivery: Automation extends to preparing and validating release candidates for deployment. You want each release candidate to be validated for stability, performance, and infrastructure security before reaching production. Typically, this consistency helps you maintain predictable release cycles without sacrificing control.
- Continuous security: Security testing should become part of daily workflows. Techniques like threat modeling and automating security during builds and releases help you spot vulnerabilities before they reach production. As we explained above, this proactive model integrates security earlier in the lifecycle, which prevents last-minute release blockers.
- Communication: Good collaboration is how you stay safe and deliver fast. Open feedback loops between developers, operations, and security teams prevent delays and create shared accountability for outcomes. According to McKinsey, teams with stronger trust, communication, and decision-making were 3.3x more efficient and 5.1x more likely to deliver results.
DevSecOps Key Components
The key components of DevSecOps include code analysis, change management, compliance management, threat modeling, and security training.
They keep security integrated and measurable across the delivery process. That’s how you create consistent protection and accountability from code to release.
Code Analysis
Code analysis validates every commit before it moves downstream. Automated static and dynamic analysis tools flag weaknesses early to reduce post-release rework.
However, accuracy matters. According to Contrast Security, over 25% of security alerts stem from false positives, and developers spend up to three hours investigating each one. Balancing automation with precision helps you keep focus on real issues.
Change Management
Change management defines how and when updates move through environments. If you integrate approval workflows and continuous monitoring correctly, your changes will be logged, reviewed, and deployed without drift or compliance gaps.
Compliance Management
Compliance management aligns your delivery processes with regulations like SOC 2, PCI DSS, and HIPAA. We advise you to automate audit trails, evidence collection, and data security checks to minimize manual overhead. Plus, it’s a good way of maintaining transparency for stakeholders.
Threat Modeling
Threat modeling identifies potential attack paths before code reaches production. When you apply it early, you can address design-level risks before they reach production. In fact, adopting structured threat modeling can reduce post-deployment vulnerabilities by up to 70%.
Security Training
Security training builds awareness of secure coding habits across your teams.
That’s important because 74% of companies reported at least one breach caused by insecure code in 2024.
You don’t want that to be you, and training helps your engineers add prevention to every task they do.
DevSecOps Roadmap
Implementing DevSecOps requires a structured, phased approach that builds security into your delivery process without slowing it down. Basically, you will integrate automation, feedback, and accountability into your existing DevOps workflow.
These are the key phases to follow:
1. Planning and Development
Security starts during planning. You can use threat modeling to identify risks before development begins and define mitigation steps as part of your sprint goals.
Do these checks early to reduce the chance of rework later and strengthen your secure software supply chain from the start. Also, integrate IDE plugins and automated code checks to have immediate visibility into potential issues before code reaches the repository.
2. Building and Testing
Testing is where you validate security assumptions. Automated tests and vulnerability scanning should run with every build to catch configuration or dependency risks. Most enterprises now treat this as a baseline expectation.
Currently, 80% of enterprise DevSecOps initiatives include vulnerability or configuration scanning tools. This shows how standard automation has become at this phase.
We also advise you to extend your tests to include runtime and container validation. That way, you can catch issues that only surface when components interact in production-like environments.
3. Operation
Once the system is live, you need continuous observation. At this stage, how quickly you detect and remediate issues directly impacts service reliability and customer trust. That’s why the most effective teams treat response speed as a performance metric rather than just a security one.
In fact, mature DevSecOps organizations resolve flaws 11.5x faster than less mature peers. This shows the value of disciplined response cycles. Ongoing monitoring improves reliability and your overall cyber posture.
4. Code Commit
This is where integration issues and vulnerabilities can enter your codebase before they’re even detected in testing. Automating validation at commit helps you block insecure dependencies, configuration drifts, or credentials pushed by mistake.
Despite this being a low-friction way to improve release security, only 12% of organizations scan every commit, even though 68% claim to have adopted DevSecOps.
But remember: if you don’t implement consistent commit-level checks, you will increase regression risk and have more security debt accumulating downstream.
5. Production
Production requires continuous validation and iterative improvement. In this phase, automation and human review need to work together. So, use AI/ML technologies for anomaly detection and behavior analysis, supported by manual reviews when necessary.
Finally, schedule penetration testing periodically to confirm that deployed controls still function effectively under real-world conditions.
DevSecOps Best Practices
Building an effective DevSecOps model requires discipline and repeatable habits.
Here are the DevSecOps best practices that help strengthen collaboration and reduce friction. Each one supports measurable improvement across releases:
- Security as code: Integrate policies, tests, and configurations directly into source control and CI/CD pipelines instead of performing manual reviews later. When you standardize checks, you can eliminate last-minute surprises.
- Iteration over perfection: Apply small, continuous updates to security controls rather than waiting for complete redesigns. Incremental testing and fast feedback loops improve resilience without slowing delivery.
- Operate like developers: Build security capabilities that developers can consume as services. This includes APIs, automated scans, or compliance dashboards that integrate with existing workflows. Typically, this approach shifts ownership from centralized security teams to shared accountability across all contributors.
- Attack and defend mindset: Adopt adversarial testing and threat modeling early in the lifecycle to expose weaknesses before deployment. Also, use red and blue team exercises to anticipate risks.
- Proactive and data-driven: The goal of this kind of continuous monitoring and anomaly detection is to identify risks before they escalate. Automation and telemetry connect incident response with real-time visibility into system behavior and risks.
- Collaboration and transparency: Encourage open communication between Dev, Sec, and Ops. Deloitte research shows that transparency fosters trust, which is important for post-mortems and feedback loops that actually improve behavior.
- Business alignment: Tie every security improvement to business outcomes like uptime, customer retention, or audit readiness. The point is for security to stay strategic instead of procedural.
DevSecOps Tools
Selecting the right DevSecOps tools determines how efficiently you can integrate security into development workflows.
For example, you need the right tools for layered testing across the pipeline. That’s how you address risks from code to runtime without disrupting release flow.
Here are the main tool categories to consider.
Static Application Security Testing (SAST)
SAST tools analyze source code to detect vulnerabilities such as hardcoded credentials, input validation gaps, or insecure dependencies. They operate early in development to give developers immediate feedback before integration.
Software Composition Analysis (SCA)
SCA tools scan open-source and third-party components to uncover known vulnerabilities and license risks. Use them to maintain visibility into dependencies and prioritize remediation before production.
Interactive Application Security Testing (IAST)
IAST tools run during functional testing to monitor live application behavior within the runtime environment. They combine the accuracy of static scans with the context of runtime data. The goal is to trace vulnerabilities directly to the affected code.
Dynamic Application Security Testing (DAST)
DAST tools simulate external attacks by interacting with live applications and APIs to identify runtime vulnerabilities. They identify issues missed by static analysis, such as authentication flaws or misconfigurations in exposed interfaces.
DevSecOps Examples
Real-world adoption of DevSecOps principles looks different across organizations, but the goal remains the same.
Here are two examples that stand out for their mature, integrated approaches:
Netflix applies resilience testing through its Chaos Monkey tool, which intentionally shuts down live production instances to test fault tolerance. This controlled disruption helps you confirm that services can recover automatically without manual intervention. The result is stronger reliability and faster recovery across distributed systems.
Adobe practices align closely with DevSecOps, even though the company doesn’t use the term explicitly. Its teams integrate automated testing, secure SDLC practices, and close collaboration between security and product engineering.
Its “think like an adversary” philosophy drives realistic attack simulations and continuous validation through red teaming, code scanning, and customer-led testing.
Besides, Adobe’s transparency builds lasting trust with enterprise clients and strengthens security outcomes. That includes publishing detailed testing reports and focusing on shared accountability.
What Are the Challenges of Implementing DevSecOps?
Implementing DevSecOps can be complex because it requires both cultural and technical transformation. In short, success depends on how well your teams adapt and coordinate across disciplines.
The most common challenges include:
- Resistance to change: Many teams still view security as a separate step rather than an integrated part of delivery. Shifting this mindset takes time and leadership support.
- Learning curve: Developers and security engineers need proficiency in automation, security tooling, and secure coding. Without proper training, adoption slows.
- Tool sprawl and cost: The growing number of platforms, scanners, and integrations makes it hard to choose the right stack and control spending.
- Cross-team coordination: DevSecOps requires synchronized collaboration between development, operations, and security. This can be difficult to maintain across distributed or large organizations.
- Complex technology landscape: Modern systems use multiple frameworks, programming languages, and architectures. Each requires continuous testing and monitoring to remain secure.
Pro tip: The key to overcoming these challenges lies in gradual adoption. You'll need to start small, automate where it adds the most value, and build shared ownership before scaling across your entire organization.
DevSecOps Trends and Innovations
The DevSecOps industry is evolving quickly as AI, orchestration, and compliance tooling reshape how teams deliver and secure software. Here are the top shifts redefining modern pipelines.
Automation and Orchestration
Roughly 80% of vulnerabilities happen from manual misconfigurations, which drives organizations toward full automation. Configuration-management and orchestration tools now help teams standardize environments, eliminate drift, and reduce manual errors. The focus is on minimizing human effort while maintaining speed and accuracy.
DevSecOps in SaaS Mode
According to Fortune Business Insight, the SaaS market is projected to grow from $315.68 billion in 2025 to $1,131.52 billion by 2032. This growth fuels the shift toward SaaS-based DevSecOps platforms that simplify setup, lower costs, and offer real-time visibility across distributed environments.
If you adopt this shift, you are promised faster collaboration and reduced operational overhead.
Of course, one disadvantage is reduced configurability compared to self-managed toolchains. SaaS platforms prioritize ease of use and scalability, but that can mean restricted access to low-level configurations, slower customization, and reliance on the provider’s security and uptime SLAs.
AI-Driven Automation
AI now supports everything from Infrastructure as Code (IaC) validation to automated testing and pipeline analytics. These tools shorten release cycles and enhance decision-making accuracy.
“AI co-pilots are reshaping coding, debugging, vulnerability scanning, and alerts… driving efficiency and productivity gains.”
- Sudhanshu Duggal, Chief Digital Officer at Procter & Gamble
Automated Incident Response and Remediation
According to Statista, cyberattacks surged in 2024, with 422 million records breached and 1,876 attacks per organization in Q3 alone. In response, many teams are adopting systems that automatically isolate affected assets and trigger remediation workflows. This helps reduce downtime and response fatigue.
Policy-Based Governance
Policy-as-code solutions now automate compliance with standards like ISO 27001 and SOC 2 in real time. These tools enforce consistent governance across hybrid infrastructures and simplify audits.
“Policy-as-code… helps with unified management and enforcement of security policies regardless of the underlying infrastructure.”
- Yuri Gubin, Chief Innovation Officer at DataArt
Streamline Your DevSecOps with Axify
DevSecOps weaves security into every stage of the development cycle. When you combine automation, shared responsibility, and ongoing validation, you shift from reactive fixes to proactive prevention.
The result is, of course, faster, safer software delivery.
But to make it work, you need strong collaboration, clear workflows, and reliable metrics that keep security aligned with development speed.
Axify can help.
Our platform links flow and DORA metrics with real-time performance insights.
Besides, our Value Stream Mapping tool gives you a clear view of your entire workflow. It highlights bottlenecks, automation opportunities, and where your security tools are delivering the most value.

As such, you can monitor throughput, stability, and recovery time to truly measure the impact of your process improvements.
Curious how better visibility can scale both speed and security? Book a demo with Axify today and see how data-driven delivery makes a difference.
FAQs
DevSecOps integrates security across the software development lifecycle. GitOps uses Git as the single source of truth for infrastructure and deployments. In short, GitOps manages how changes are deployed, and DevSecOps governs how those changes stay secure. Together, they form a complementary approach to safe, automated delivery.
Pro tip: Check out our article on GitOps vs. DevOps to see how both approaches align in modern delivery pipelines.






.png?width=60&name=About%20Us%20-%20Axify%20(2).png)


