You’re under pressure to deliver quickly, but you can’t afford to let anything fall through the cracks. You understand the risks of leaving security issues until the last minute. That’s why more teams like yours are changing their mindset and updating their software development lifecycle to include security from the start.
In this article, you’ll learn proven DevSecOps best practices to help you integrate security into every stage of development, from design and coding to testing and deployment. You’ll discover how to improve your development process without slowing down delivery or overloading your team with extra steps.
So, let's take the first step and explore what DevSecOps is.
What Is DevSecOps?
DevSecOps stands for Development, Security, and Operations. It’s your way of building security right into the software development life cycle, instead of saving it for the end. You bring your security team into every step, from design to deployment, so you catch potential vulnerabilities before they grow into real threats.
Around 36% of companies already follow this model. The global DevSecOps market was valued at $8.84 billion in 2024 and is set to grow 13.2% annually through 2030. As adoption grows, you're seeing tighter security controls within fast-moving DevOps pipelines without slowing down your team.
Now that you’ve got the definition down, let’s see how DevOps evolved into DevSecOps.
DevOps Security Best Practices
If you're serious about improving security without slowing down your delivery, you need smart, practical steps. These aren’t vague suggestions, but proven ways to bake security into your day-to-day work. Here are the ones that will make the biggest difference for your team.
To help you take action, let's take a look at the four main areas where you can apply these best practices, one by one.
Development & Deployment DevSecOps Best Practices
The earlier you bring security into your pipeline, the fewer surprises you'll deal with later. Here are the best practices that help you shift security left and build it into your everyday work.
1. Shift Left
You can start by adding security to your design and development stages, not just testing. When you shift left, you catch problems early and fix them faster.
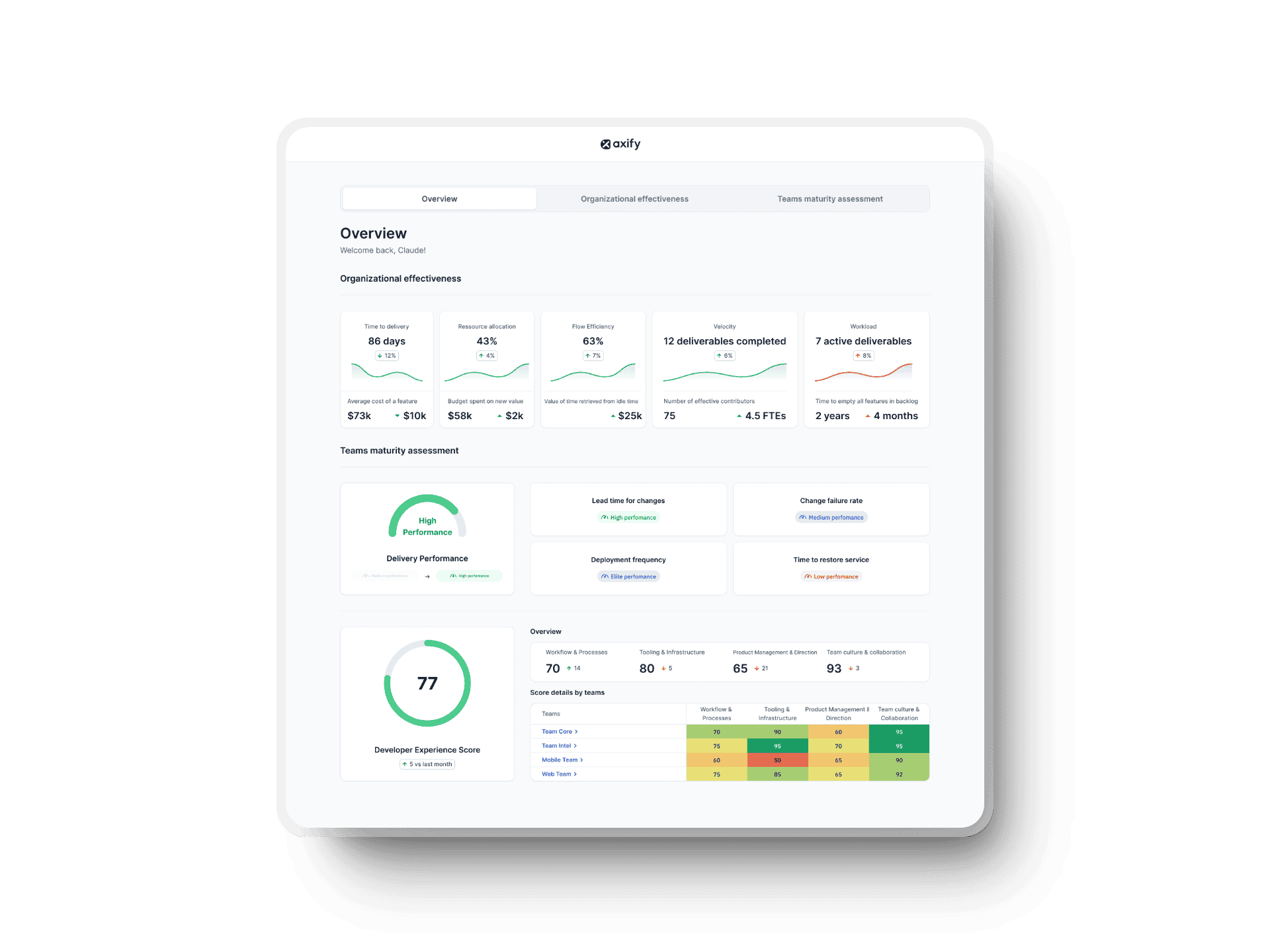
Newforma, one of our clients, saw a 22X boost in deliveries by doing just that. They used Axify to map their flow, inspect bottlenecks, and speed up release cycles.
Watching metrics through Axify’s VSM and DORA dashboards allowed this company to act fast without cutting corners. You can do the same if you get your team involved early, and you’ll reduce the effort it takes to fix security flaws later in the game.

2. Implement Secure Coding Standards
Normally, you can write safer code just by sticking to smart, language-specific rules. The issue is that despite training, 67% of devs still knowingly push code with vulnerabilities. So, make sure to set coding guidelines that match real-world threats and back them up with automated checks.
Tools like Static application security testing (SAST) can connect right into your continuous integration pipeline and flag potential issues before they hit production. This way, you're not slowing anyone down or asking devs to do extra manual work.
It’s fast, clean, and dependable. But keep in mind that just following the rules isn’t enough if you don’t check your code every step of the way.
3. Provide Security Training for Developers
Your code is only as secure as the people writing it. A recent OpenSSF report found that 28% don’t understand secure coding practices, and 53% have never taken a security course.
That’s why security training matters. If your developers don’t know what to watch for, they’ll miss common threats like XSS or insecure dependencies. You can share resources like the OWASP Top 10, hold quick sessions, or just bring awareness into team rituals. You don’t need a bootcamp, just start with what matters.
4. Adopt Automation in the CI/CD Pipeline
Manual reviews slow things down. We’ve seen it firsthand where large enterprises usually wait 15 to 25 days just to push changes through all the approvals. Fragile testing setups only make it worse when teams still rely on humans to check what machines should already be doing. That’s where automation saves the day.
Using automated security testing in your CI/CD pipeline enables you to run scans, apply policies, and secure your builds without bottlenecks. That’s why the smartest 29% of companies have already automated over 70% of their security testing.
Axify’s VSM shows where manual delays occur and highlights which stages could benefit most from automation.

In fact, two teams at the Development Bank of Canada used Axify to cut pre-development time by 74% and quality control time by 81%. This proves how automation and better visibility can drive faster, more efficient delivery.
5. Implement Continuous Security Testing
You can’t rely on one-off scans. If you’re serious about reducing potential security risks, you need consistent, repeatable checks in place. That means combining static application security testing (SAST), dynamic application security testing (DAST), and software composition analysis (SCA) throughout your builds.
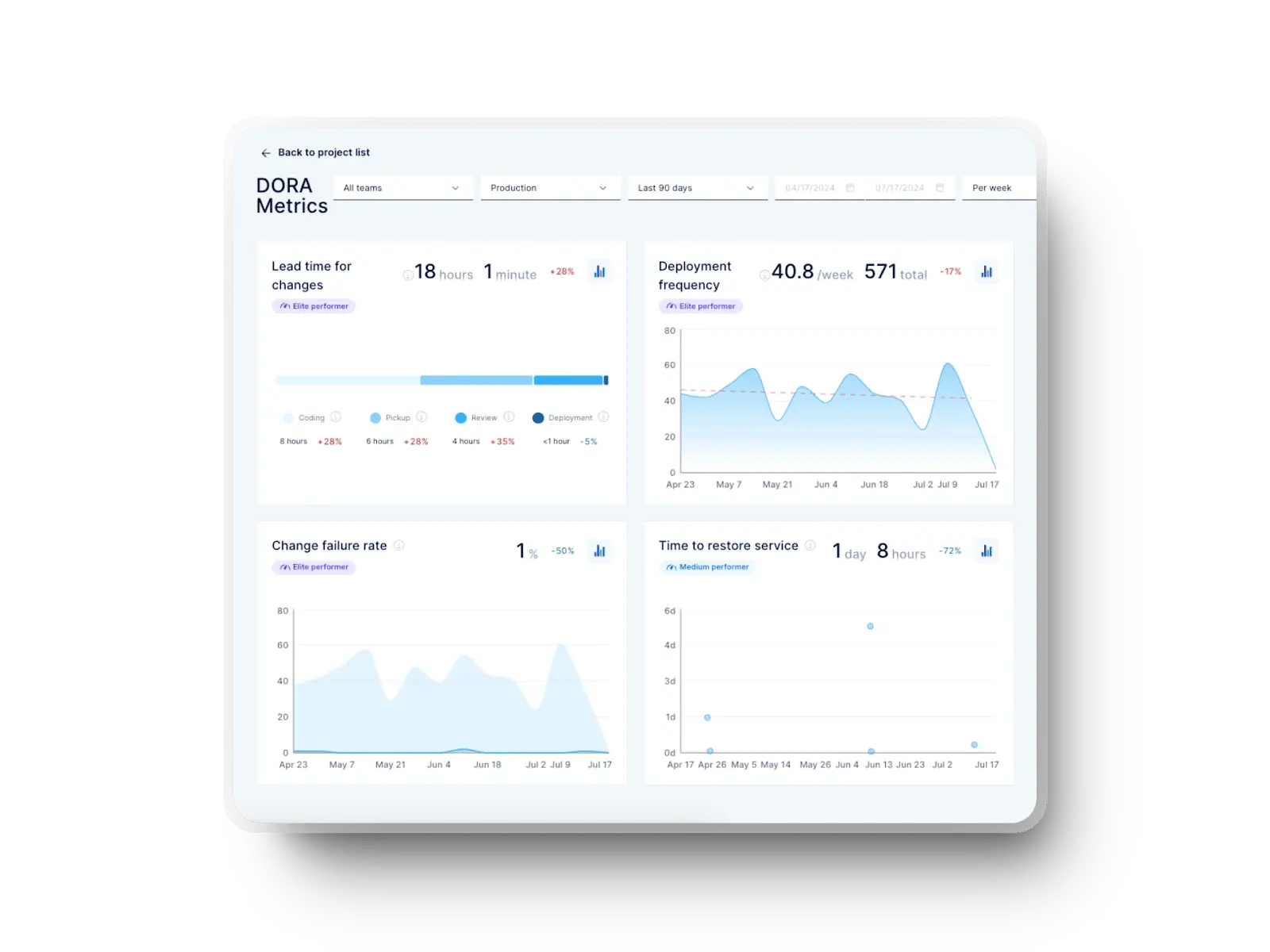
Naturally, you should test every layer so you’re not leaving gaps, such as code, dependencies, and behavior. Axify helps DevSecOps teams track delivery delays and unstable workflows through metrics like Cycle time, deployment frequency, recovery time, change failure rate, and lead time for changes. This makes it easier for you to spot when testing phases are slowing things down.

You’re not alone in this shift either. 44% of organizations now run security tests every week or more frequently. This shows how quickly the industry is moving toward continuous testing.
6. Use Threat Modeling and Risk Assessments
Without a doubt, you know your system better than anyone, so use that knowledge to spot potential threats before they hit production. Threat modeling is the process. Unfortunately, only 33% of U.S. firms have complete enterprise risk management plans. That’s a huge gap you can close with better prep, better tools, and better follow-through
To create a solid threat modeling plan, you need the right people on your team.
A recent report showed that 90% of companies include at least 11 people in their threat modeling sessions, with some involving over 30. These people include engineers, security analysts, product managers, QA leads, and even customer success reps. That’s basically anyone who touches the system or understands user behavior.
Next, you can map your flow, identify weak spots, and determine what a malicious actor would target first. Then, build around that. For example, the most effective models simulate real-world attacks and ask: “If I were the attacker, where would I strike first?” From there, you prioritize what to protect, how to detect early signals, and what to do when something slips through.
7. Use Infrastructure as Code (IaC) for Security
When managing infrastructure manually, mistakes are bound to happen. With IaC tools, you eliminate that risk by scripting the setup and establishing secure defaults. This allows you to control who can make changes and enables your team to reuse the same safe setup repeatedly. It’s also simpler to run security scanning tools on templates than on ad hoc environments.
Here’s a more detailed look at IaC:
However, there’s still work to be done, as only 13% of companies have achieved maturity with IaC. If you’re just starting out, look on the bright side: you have the opportunity to get ahead by building repeatable, secure foundations from day one and scaling based on data.
8. Leverage Immutable Infrastructure
Manual changes introduce risk and uncertainty.. That’s why immutable infrastructure works better. You build it once, test it thoroughly, and then replace it entirely, rather than patching it. It’s safer and makes rollbacks easier.
According to DevOps.com, this approach nearly eliminates configuration drift, which is crucial in cloud-based and DevOps process environments where things change fast. You’ll avoid weird bugs, hidden risks, and unexpected behavior.
Plus, your operations teams will appreciate having predictable, well-tested systems they can count on during high-pressure deploys or late-night incidents.
9. Prioritize Container Security
Containers let you ship fast, but they also create blind spots if you’re not careful. You can start by using trusted container images, then scan them early and frequently. Runtime protection matters too, so add controls that block unexpected behavior once they’re live.
Only 34% of small and medium-sized businesses are doing this right now, so you’ve got a clear edge if you start now. You can use Axify’s CIO dashboard, DORA metrics, and VSM to help you track delivery performance and spot delays. These could stem from issues like failed deployments or unstable builds, including those related to container problems.
If you take our advice and make container safety a habit, you’ll reduce downtime and keep your stack clean as you scale.
Access & Policy Management Best Practices
To keep your systems tight and your attack surface small, you need strong access policies that actually work in real-world environments. Here are the best practices to follow.
10. Enforce Access Controls and Least Privilege
Provide your users and services only what they need, nothing more. Essentially, you reduce exposure by using role-based access control and adjusting privileges based on actual roles, not assumptions.
Two out of three companies already consider least privilege essential, which shows how critical it is for your strategy. But there’s still a gap. According to the 2021 Identity and Access Management Report, 77% of organizations grant users more access than they actually need, which is a risky practice.
While Axify doesn’t manage access controls directly, its Workflow Stability and Delivery Tracker highlight where work stalls, including delays caused by misconfigured permissions or access issues, so you can fix blockers early and avoid unnecessary risks.

11. Leverage Policy as Code
You don’t want policy decisions buried in docs or tribal knowledge. Using Policy as Code allows you to write, test, and enforce security policies right in your development tools. This gives you repeatable controls and faster audit results.
According to the 2023 State of Policy as Code Report, 94% of organizations now view Policy as Code as a key part of their future.
More interestingly, banks are already ahead of the curve. A study on 22 financial institutions showed frameworks like OPA and Styra DAS lead to stronger governance and lower latency.
Axify helps you understand how delivery is affected by delays, including those introduced by policy checks. The first important step is visualizing team flow and wait time across your deployment pipeline.
12. Automate Ticket Creation and Tracking for Security Issues
It’s not enough to find common vulnerabilities because you need a clear path to fix them. Automating ticket creation for security alerts helps your security team take fast, consistent action.
You also cut the time between detection and resolution. According to IBM, this automation ensures critical Common Vulnerabilities and Exposures (CVEs) get prioritized and resolved quickly, which makes a huge difference in your overall security posture.
With Axify’s VSM and CIO dashboard, you can track where work stalls in the pipeline and see which teams may need help resolving blockers, including unresolved security issues. This approach saves time, reduces risk, and helps you meet your regulatory requirements more easily.
Monitoring, Observability & Response Best Practices
To respond faster and smarter to risks, you need to see what’s happening inside your systems at all times. Here are the practices that help you get there.
13. Increase Security Observability
When you track logs, metrics, and system behavior consistently, you’re watching and understanding. Strong continuous monitoring gives you the visibility to catch issues before they grow.
According to the 2023 State of Security Observability report, 67% of teams saw better data confidentiality through observability. Even more, 64% cut their response times, and 70% improved detection speeds.
Axify’s DORA metrics and flow insights give you visibility into your software delivery process to see potential delays, detect patterns, and make faster, informed decisions without adding extra overhead. It’s how you gain control fast.
14. Implement Real-Time Security Monitoring
You can’t afford to wait hours or days to detect an issue. Real-time monitoring helps your security tools spot suspicious behavior the moment it happens. That’s more important now than ever because cyberattacks rose by 30% in 2024, with companies facing over 1,600 attacks each week.
But only 20% of businesses actually monitor their cloud posture in real time. That leaves a gap. With Axify’s CIO dashboard, you can track delivery performance and production delays, which complements insights from your security monitoring tool. A multi-pronged approach like this is how you stay agile because you can quickly spot where potential issues might affect releases.
15. Conduct Regular Security Audits and Compliance Checks
Today, 37% of companies run internal audits yearly. What's even more impressive is that 91% plan to adopt continuous compliance within five years. It’s no wonder that happens because audits help you check a box and stay ready.
Comparing your systems to standards like SOC 2 or ISO 27001 and running penetration tests allows you to strengthen your defenses.
While Axify doesn’t perform audits, it can support your efforts. For example, you can fold these checks into your daily work by using Axify to surface delivery insights. These will help your team stay aligned with broader compliance goals from the start.
Let’s say your company is working toward SOC 2 certification. Part of that means proving consistent, well-documented delivery practices. With Axify, you can track metrics like lead time, change failure rate, and deployment frequency, giving you tangible evidence that your processes are stable and repeatable. That kind of visibility helps compliance teams and auditors trust what they see without slowing engineering down.
16. Expand Incident Response Capabilities
A quick response can save you from a full-blown crisis. You can build clear escalation paths, automate alerts, and rehearse with your team. If you do this right, you’ll make smarter decisions under pressure.
Again, Axify doesn’t have incident response capabilities, but it can surface delays, blockers, and unusual patterns in delivery, so you know where your weak points are. For example, if a team’s lead time suddenly spikes or deploy frequency drops, it might signal underlying issues, like brittle code, burnout, or hidden rework. All these issues could turn into incidents down the line, so it’s better to be proactive about them.
17. Leverage Red Teams, Blue Teams, and Bug Bounties
Simulated attacks help you test defenses like a real attacker would. Red teams push your limits. Blue teams defend. Bug bounty programs bring outside eyes into your system. Together, they give you a clearer picture.
This is how you can get started with red teaming and blue teaming in cybersecurity:
About 72% of teams run red team tests, and 60% use blue teams. What’s more, 74% of security professionals saw stronger systems after testing, with 18% reporting major funding increases.
These aren’t just drills. They’re how you stay sharp. Back it with Axify’s flow insights and you’ll pinpoint delivery weak spots faster. This can help your teams act on the findings of the red and blue teams.
Let’s say one of our clients keeps seeing incidents tied to rushed hotfixes and unclear ownership during releases. Here’s how they could use Axify as part of the solution.
After a red team exercise exposes how fast a bad actor could exploit a misconfigured endpoint, the blue team patches the gap, but they also trace the root cause to a last-minute deploy. With Axify, the client digs into delivery metrics and sees a pattern: high cycle time and unresolved work-in-progress piling up before each Friday release.
By surfacing those trends, Axify helps them redesign their process, spreading work more evenly across the week, assigning clearer DRI ownership, and adding tighter reviews.
So now, when red and blue teams flag something, there’s already a system in place to prevent repeat mistakes.
Operational and Cultural Best Practices
Building a secure software environment takes more than good tools. It takes a cultural shift, one where every team feels responsible for what they ship. Here are the habits that help make that happen.
18. Collaborate Across Teams
You can't build secure software in isolation. Security isn't just one team's job but everyone's. You need to build shared habits across your Dev, Ops, QA, and security teams. That starts with making security practices part of daily workflows and conversations.
You should invite security experts into design discussions. Make QA aware of new threat models. In Axify, you can use Value Stream Management and DORA metrics to spot breakdowns in communication. Fixing those improves delivery and strengthens your team’s alignment.
“Great things in business are never done by one person. They’re done by a team of people.”
- Steve Jobs, Co-founder of Apple Inc.
19. Promote a Security-First Workplace Culture
Culture builds behavior. If your team treats security as a one-off checklist, they’ll overlook critical risks.
The statistics are dire, though. 62% of companies lack strong security awareness programs, and 45% of employees report never receiving any security training at all. But if you bake security into habits (like daily standups or sprint reviews) and it becomes part of your team’s language, better decisions follow.
For example, use Axify’s Daily Digest to bring up high-risk or delayed items during your dailies. These could include work affected by unresolved security tasks to help you address risks before they snowball.

20. Invest in Security-Aware Workflows
Strong workflows catch issues before they become problems. You need processes that flag security considerations throughout the entire software development lifecycle. That means scanning earlier, reviewing risks during planning, and using metrics to track impact.
Axify allows you to break down workflows by stage using VSM, so you know where bottlenecks occur and where risks (including those tied to security tasks) might be slowing things down. This investment pays off fast.
In fact, small companies can get a 69% ROI from security training programs, while larger organizations see returns as high as 562%. But those training programs do nothing if you lack the right tools and clear processes. Ultimately, that’s what genuinely helps security and delivery.
21. Consider the Full Application Life Cycle
Think beyond just build and deploy. Security must stay active from design all the way to retirement. Include every stage of development, from architectural planning to offboarding old systems. You should assess security requirements during initial design, then revisit them when sunsetting apps.
With Axify, you can take a long view of your engineering health. The Objectives dashboard helps teams stay aligned on long-term goals, like reducing lead time or increasing deployment reliability, which supports more secure, predictable development over time. Meanwhile, Workflow Stability shows how consistently work is flowing across sprints, so you can catch signs of team overload or delivery volatility before they introduce risk.
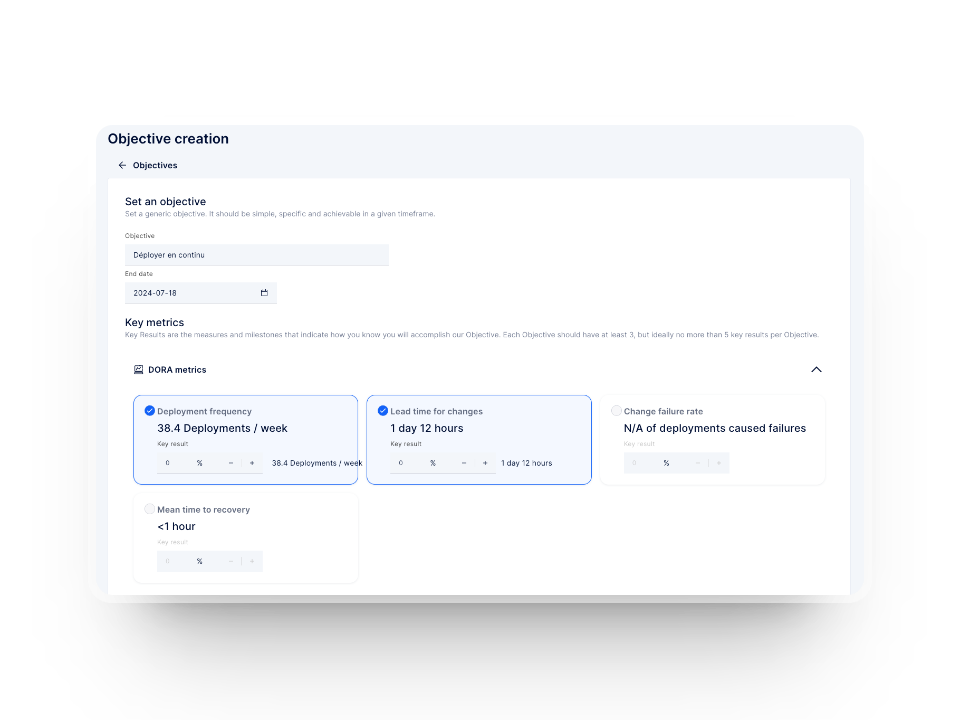
Covering the entire development lifecycle allows you to reduce the risk of security breaches slipping through unnoticed.
22. Update Your Tools Regularly
Outdated tools are open doors, so it’s critical to keep your security testing tools, libraries, and frameworks up to date. In other words, you should automate patching when you can.
Here’s just one example of how you can get started.
Axify helps by identifying quality issues through DORA’s Change Failure Rate and Failed Deployment Recovery Time. You can use these insights to decide if tool upgrades are needed to improve speed and safety.

This matters because 32% of cyberattacks take advantage of unpatched software, and a shocking 81.5% of projects still use outdated libraries even after advisories. But if you stay current, you can also stay protected.
23. Reduce Engineering Workload via Smart Automation
Manual work slows teams down and creates space for errors. With Axify, you can reduce tedious work by surfacing delivery risks like idle or delayed pull requests, so your team can focus on the items that need attention.
You can also use the CIO Dashboard to monitor team load and see if your engineers are spending more time fixing than building. Then, you can shift efforts to where they matter most.
Smart automation works. That’s why 76% of businesses now use it to reduce manual tasks and improve consistency. Less grunt work means more focus and better results for both speed and secure applications.
Streamline DevSecOps Best Practices with Axify
DevOps teams that take a proactive approach and share responsibility for security can better protect the production environment from unexpected risks.
Axify allows you to cut through the noise and focus on what helps your development team build safer, faster, and smarter. You’ll spot blockers early using Value Stream Mapping, monitor DORA metrics across teams, and reduce manual processes through smart automation.
Axify gives you visibility into your software delivery process by helping you improve the flow without creating more work. You won’t get a magic fix for every risk, but you will have tools to build strong habits and reinforce your approach to security across all stages. That’s how you create lasting change without slowing down.
See how Axify can improve your team’s delivery and security. Book a free demo now.






.png?width=60&name=About%20Us%20-%20Axify%20(2).png)



